Disable Desktop Cleanup Wizard Login Script Windows 7

You are here: » VDI optimization script (part 1) In the summer of 2010 Erik wrote an article about “How to: Optimize guests for VMware View” in which he describes all sorts of changes he makes for a Windows XP or Windows 7 virtual desktop in a VDI environment. The changes that are suggested in the article are still valid, but after reading them I was wondering if there are new additions, specifically with Windows 8 now on the market. During my search I quickly came across a Visual Basic script that was released by Microsoft on their Technet site for optimization of a Windows 8 virtual desktop. At the beginning of the script there is a disclaimer that you should have knowledge of the vb scripting language and that you should proceed with caution. Since the script is fairly long and a lot of changes are being made I decided to break the script down and put this in a table to give an overview of the services and settings being changed. As the title of the article indicates this is part 1 of the article, in part 2 I will try to explain the different pieces of the script in such a way that more people might understand what is happening inside the script.

While putting everything into a table I also looked if these changes could be made for a Windows 7 desktop too.
Irish Terrier Puppies For Sale AlbertaThe table is divided in several parts (and one bullet list) to provide some more overview to the whole.
Puppies For Adoption In Franklin Tn Block Level Backup Engine
Houses For Sale Tw14 Distributed Link Tracking Client Function Discovery Resource Publication Microsoft Software Shadow Copy Provider Secure Socket Tunneling Protocol Windows Connect Now – Config Registrar Windows Media Player Network Sharing TCP/IP / Large Send Offload NTFS Last Access Timestamps Machine Account Password Changes UAC secure desktop prompt

AutoUpdate of drivers from Windows Update IE First Run Wizard Ability to clear the paging file during Run with adjusted settings – Customer Experience Improvement Program\BthSQM – Customer Experience Improvement Program\Consolidator – Customer Experience Improvement Program\KernelCeipTask – Customer Experience Improvement Program\Uploader – Customer Experience Improvement Program\UsbCeip – Power Efficiency Diagnostic\AnalyzeSystem – Windows Filtering Platform\BfeOnServiceStartTypeChange – Windows Media Sharing\UpdateLibrary Window contents when dragging Show translucent selection rectangle Use background image for each folder type Use drop shadows for icon labels on the List box smooth scrolling Active windows tracking Z order Hopefully the tables provide you with an overview that can help determine which settings might be useful for your VDI environment.

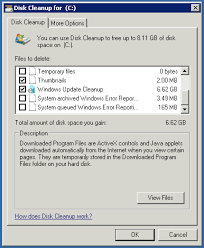
In the next part I can hopefully explain the script in some more detail so that you can use it yourself. VDI optimization script (part 2) » « Why visit VMworld 2013?FacebookTwitterRedditWhatsAppGoogle+BufferLinkedInPin ItIn Microsoft Knowledgebase article KB978980 Microsoft states that when there are more than four broken shortcuts on the desktop, the System Maintenance troubleshooter automatically removes all broken shortcuts from the desktop. It implies that it only removes "broken" shortcuts.Look at this screenshot. The above dialog says that the System Maintenance cleans "unused" files and shortcuts. Does it mean that it removes unused (but working) shortcuts that are pointing to a valid target file/folder? At this stage we need more clarity on what the System Maintenance cleans (only the broken shortcuts, or does it clean valid shortcuts that are kept unused.) And, does the System Maintenance tool store the unused / broken shortcuts in a different folder, similar to the Desktop Cleanup Wizard in Windows XP?

I’ll post back my findings in due course. Also, I’d love to hear the insights from our valuable readers in the meantime.UpdateIt’s now clear the the troubleshooter deletes broken shortcuts as well as unused (in 3 months) ones. This article is intended for IT administrators. If you are an end-user, please contact your support desk to run the Receiver Cleanup Utility. Receiver cleanup utility is not required and not recommended while upgrading to the Receiver for Windows 4.4. Receiver for Windows 4.4 can upgrade from any older version of Receiver without the need of using the clean up utility. Clean-Up utility is designed to assist with the following scenarios: When errors occur during upgrade from an earlier version of Receiver or Online Plug-in When unexpected behavior or performance is experienced after upgrade from an earlier Receiver or Online Plug-in If Receiver upgrade is not possible due to feature incompatibility and/or a clean uninstall is required

The Receiver Clean-Up Utility removes components, files, and registry values of Online Plug-in 11.x, 12.x, and Receiver for Windows 3.x, 4.x (Online Plugin-in 13.x, 14.x). Offline Plug-in component if installed. Supported Operating Systems (32- and 64-bit unless noted) Windows 2008 R2 64-bit Read, write, and modify access permissions are required for the following: Local machine registry (HKLM) Local user registryDefault user profile on computer %programfiles%\citrix on 32-bit systems or %programfiles(x86)%\citrix on 64-bit systems Go to Microsoft article How to backup and restore the Registry in Windows for backing up the registry. How to Use the Citrix Clean-Up Utility The Receiver Clean-Up Utility is a standalone executable file and does not require installation. Although the Receiver Clean-Up Utility will backup Receiver registry keys before deleting them, it is recommended to back up the registry

before running this tool. Go to Microsoft article How to backup Caution: Always back up the registry. Run the Receiver Clean-Up Utility with administratorRestart the machine when the utility Note: The Receiver Clean-Up Utility can be run in unattended mode if desired using the /silent command line option. ReceiverLogs folder is created in the location where the utility is run and tracks all uninstall actions and results. NOTE: In order to improve the Citrix Receiver experience, users will be prompted to select Y or N to upload the Receiver Clean-Up utilityPlease be sure to click OK to accept the Data Collection and Privacy policy. Data Modified by Receiver Clean-Up Utility The utility terminates all Receiver processes prior to running theRefer to the ReadMe file included with the tool for a list of items that will be removed during the clean-up process. How to Undo the Changes Made by Receiver Clean-Up Utility The Receiver Clean-Up Utility creates a backup of all Citrix registry
keys in the file \ReceiverLogs\RegBackup.reg before running any clean-up and deletion process. To undo the changes: Reinstall Receiver for Windows Import the RegBackup.reg file to restore settings and customizations in the Uninstalling Receiver Clean-Up Utility Delete the downloaded executable and config.xml files from the current directory, and if desired delete the files in the ReceiverLogs folder. The Receiver Clean-Up Utility does not support non-Administrator users with roaming profile. If Receiver is not installed at the default location, the Receiver Clean-Up Utility might not work properly. Receiver Clean-Up Utility is not recommended if environment has Windows Receiver 4.3 (or above). to Remove Client Files Remaining on System after Uninstalling Receiver for Windows CTX134237 - How to Remove Files Remaining on System after Uninstalling Receiver for Mac Downloads - Citrix software applications are provided to you as is with no
representations, warranties or conditions of any kind. You may use and distribute it at your own risk. CITRIX DISCLAIMS ALL WARRANTIES WHATSOEVER, EXPRESS, IMPLIED, WRITTEN, ORAL OR STATUTORY, INCLUDING WITHOUT LIMITATION WARRANTIES OF MERCHANTABILITY, FITNESS FOR A PARTICULAR PURPOSE, TITLE AND NONINFRINGEMENT. generality of the foregoing, you acknowledge and agree that (a) the software application may exhibit errors, design flaws or other problems, possibly resulting in loss of data or damage to property; (b) it may not be possible to make the software application fullyand (c) Citrix may, without notice or liability to you, cease to make available the current version and/or any future versions of the software application. In no event should the code be used to support of ultra-hazardous activities, including but not limited to life support or blasting activities. NEITHER CITRIX NOR ITS AFFILIATES OR AGENTS WILL BE LIABLE, UNDER BREACH OF CONTRACT OR ANY OTHER THEORY